What Is CSV Injection ?
It is not uncommon for applications to export data in comma-separated-values (CSV) format for subsequent analysis or downstream processing. Many times that later processing includes viewing and analyzing the exported data in Microsoft Excel or Google Sheets.
CSV Injection, also known as Formula Injection, describes a vulnerability arising from this scenario, in which untrusted input is exported directly to comma-separated-values (CSV) files as data for subsequent import into a spreadsheet. Such input can be maliciously crafted to break the data/code barrier in spreadsheet software and result in unintended command and program execution.
Spreadsheets and Formulas
We will use Microsoft Excel for our examples, while noting that similar vulnerabilities exist in Google Sheets.
Microsoft Excel is ubiquitous and is the de-facto standard for spreadsheet processing, and has long supported the ability to open and read CSV files. In fact, in many user-environments, the default program for processing a file with a .csv extension is Excel.
A comma-separated value file is very much what it sounds like, with each line becoming a spreadsheet row, and each comma-delimited value used to populate the cells of the corresponding row.
CSV Example
A file (OneTwo.csv) containing the following lines:
1, 2, Buckle, My Shoe 3, 4, Shut The, Door
appears as the following (partial screenshot) when opened with Excel:
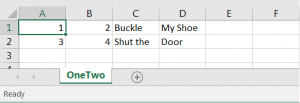
Thus far, this is the happy path; nothing but data. The twist comes with the fact that Excel is also perfectly happy to accept formulas as cell values:
A file (OneTwo.csv) containing the following lines:
1, 2, Buckle, My Shoe
3, 4, Shut The, Door
Today is:,=today(), Tomorrow is:,=today()+1
illustrates how Excel quietly executes the formulas, displaying the calculated dates as numbers:
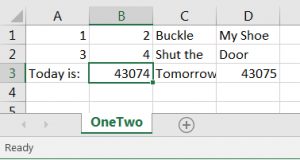
Changing the format of the cells to “Short Date” format will result on the display below, showing that the certain cells have been configured as formulas:

CSV File that Invokes a Program
The fact that formulas can be imported may be useful under certain scenarios, but it allows an attacker to craft malicious cell content such as:
1,2,Buckle,My Shoe
3,4,Shut the,Door
Today is:,=today(), Tomorrow is:,=today()+1
This opens the calculator:,=calc|a!z
The obscure code on the end (and I agree it is about as obscure as it gets), is explained here and here, and uses Microsoft’s DDE (Dynamic Data Exchange) protocol to launch the standard Windows calculator program. Without getting bogged down in the syntax, this demonstrates the ability to launch any program that can be launched via DDE. Granted, as a security measure, Microsoft requires the user to acquiesce and first declare their trust of the file , but remember, this is a CSV file –users do reasonably expect it to initiate programs or commands.
Our final example shows the generalized form of the exploit that can be used to run any program from the command line, once again with the provision that the user must agree they trust the file:
1,2,Buckle,My Shoe
3,4,Shut the,Door
Today is:,=today(), Tomorrow is:,=today()+1
This opens the calculator:,"=2+5+cmd|' /C notepad'!A0"
CSV File that Exposes Spreadsheet Data To The Web
Another exploit that requires less trust from the victim is to embed a link within the document that will export spreadsheet content right out of the organization. The following syntax, when it is loaded from a CSV file into a cell will display the error message as a hyperlink to the user, that when clicked will quietly transfer the contents of the indicated cells:
Accept: */*
:
CSV Injection Vulnerability Summary
CSV Injection stems from the fact that CSV files can contain cell values that represent formulas and that those formulae can be maliciously crafted to unintentionally execute code and/or interact with hostile web-resources. Clearly, care must be taken when importing untrusted CSV files into spreadsheet applications. We would deem a CSV file to be trusted only if it was produced by an application under our control that we know with certainty does not produce cells containing formulas. (Note that the former does not imply the latter.)
For additional insight into how to discover CSV Injection vulnerabilities in your web-applications, please see the article entitled: “How to Test For CSV Injection“.
For additional insight into how to prevent or fix HSTS vulnerabilities, please see the article entitled: “How To Prevent CSV Injection“.
Some additional information on CSV Injection can be found here, here, and here.
About Affinity IT Security
We hope you found this article to be useful. Affinity IT Security is available to help you with your security testing and train your developers and testers. In fact, we train developers and IT staff how to hack applications and networks.
Perhaps it was a network scan or website vulnerability test that brought you here. If so, you are likely researching how to find, fix, or avoid a particular vulnerability. We urge you to be proactive and ensure that key individuals in your organization understand not only this issue, but also are more broadly aware of application security.
Contact us to learn how to better protect your enterprise.
Although every effort has been made to provide the most useful and highest quality information, it is unfortunate but inevitable that some errors, omissions, and typographical mistakes will appear in these articles. Consequently, Affinity IT Security will not be responsible for any loss or damages resulting directly or indirectly from any error, misunderstanding, software defect, example, or misuse of any content herein.


